In my networking class studies, I have been learning a range of topics, from firewall design and implementation, designing a screened subnet (DMZ), configuring intrusion detection devices (such as Snort), and more.
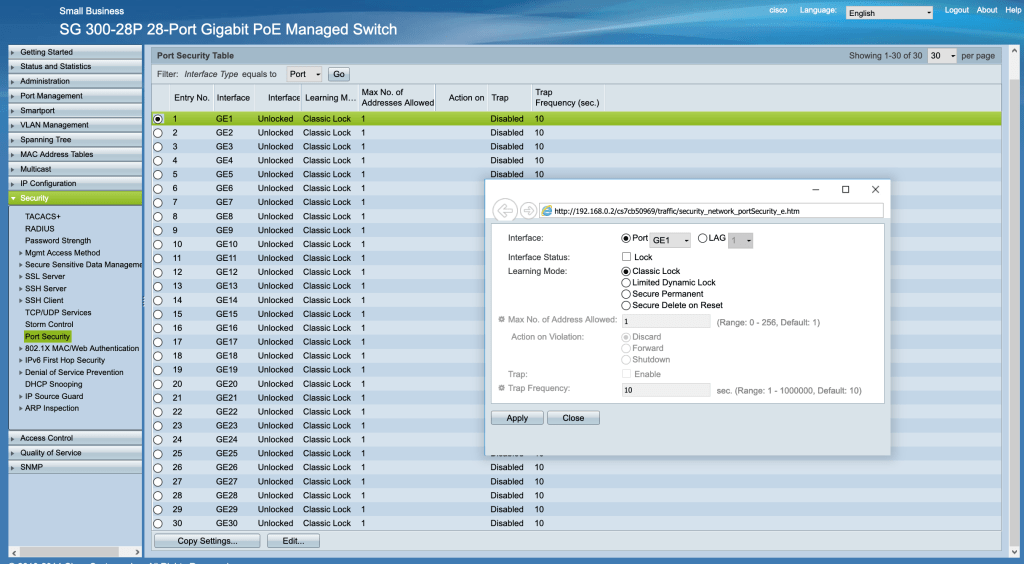
Today I have diving deep into the world of switching and routing, such as configuration of switches, including that of switch ports – locking them down against unauthorized access or other malicious behaviors.
One suggested approach to harden switches from these kinds of vulnerabilities includes disabling unused ports. In an example switch’s configuration options, accessed via console, unused ports can be togged to the down option, thus closing off that port’s availablity:
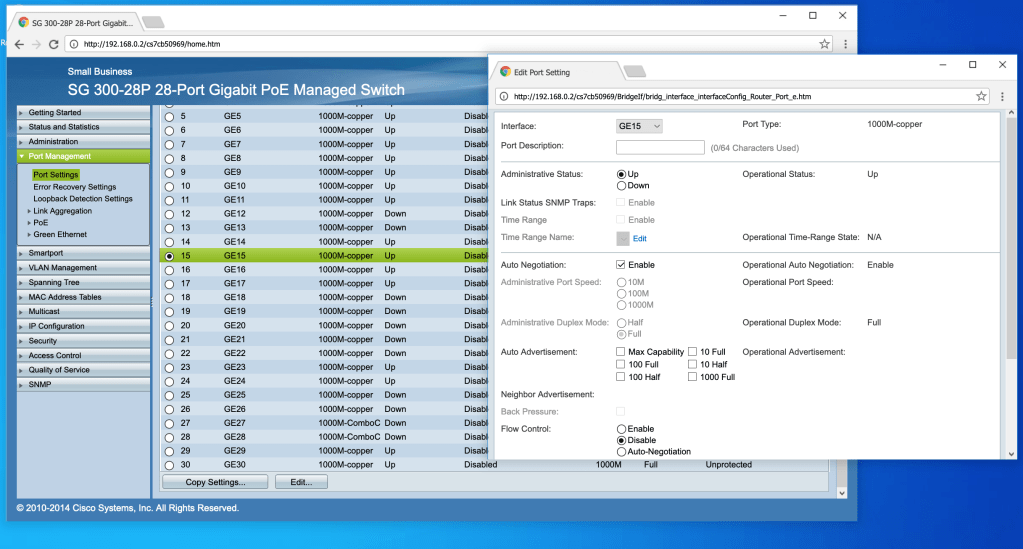
After configuring that specific port, that configuration can be copied (‘Copy Settings’ button on the bottom), and applied to other ports as specified. In this way, the switch can be hardened against this specific form of intrustion.
Besides locking down ports, switches can be hardened by ensuring updated firmware and patches, and the use of ACL lists (MAC, IPv4 and IPv6). In addition, the switch can be configured so that a port is limited to a particular device. Here’s an example of this configuration: