Some of the foundational security concepts include the CIA Triad (confidential, integrity, availability) of data, identification/authentication/authorization, and AAA (authentication, authorization, accounting). A user provides an identity, confirms and authenticates that identity through a variety of means, and subsequently, after providing the identity, is allows appropriate access to resources.
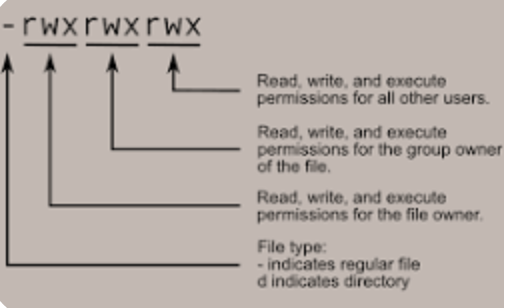
Discretionary Access Control (DAC) is what I’ve been doing with Linux files- using ‘chmod’ commands, for example, to add or remove read/write/execute. This is similar to Rule Based Access Control, which is the approach for creating and using Access Control Lists (ACL), used by network edge resources, such as firewalls or routers.
Alternative models/approaches include Mandatory Access Control (MAC), where every object is assigned a label, and every user has an assigned level – a resource is made available to a user, or not, depending on the matching of those two, Role Based Access, where users are placed within groups which are assigned access permissions to resources, or Attribute Based Access, which gives flexibility as a variety of attributes can be assigned to a resource and then ascertained whether the subject has the same attributes thus giving access.